
The National Security and Defense Council (NSDC) of Ukraine is accusing threat actors located on Russia networks of performing DDoS attacks on Ukrainian government websites since February 18th.
The National Coordination Center for Cybersecurity (NCCC) at the NSDC state that these DDoS attacks have been massive and have targeted government websites in the defense and security sector.
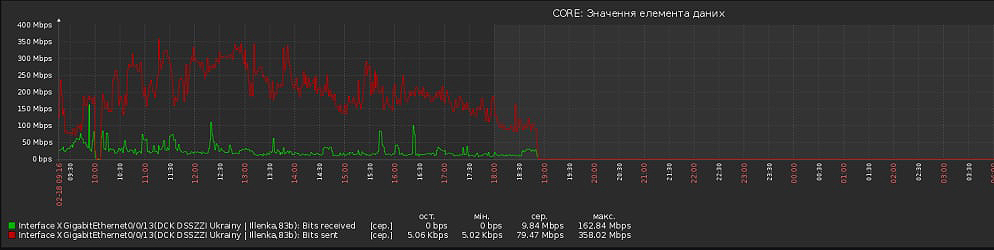
Source: NCCC
While Ukraine did not directly accuse Russia of the denial of service attacks, they stated that the attackers’ IP addresses were located on Russian networks.
“In particular, attacks were carried out on the websites of the Security Service of Ukraine, the National Security and Defense Council of Ukraine, resources of other state institutions and strategic enterprises. It was revealed that addresses belonging to certain Russian traffic networks were the source of these coordinated attacks,” the NCCC stated in a press release Monday morning.
The NCCC states that their investigations uncovered a new malware planted on vulnerable Ukrainian government servers that adds the devices into an attacker-controlled botnet. These devices are then reportedly used to perform further DDoS attacks on other Ukrainian sites.
“In such a way, during an attack, vulnerable government web servers are infected with a virus that covertly makes them part of a botnet used for DDoS attacks on other resources.”
“At the same time, security systems of Internet providers identify compromised web servers as a source of attacks and begin to block their work by automatically blacklisting them. Thus, even after the end of the DDoS phase, the attacked websites remain inaccessible to users,” explains the NSDC explained.
The NCCC has not provided any IOCs related to this malware.
Possible retaliation for Egregor ransomware arrests
Last week, news leaked that Ukrainian law enforcement, in cooperation with the US and French police, arrested alleged Egregor ransomware operation members.
Three days later, the Security Service of Ukraine (SBU) issued a press release about the Egregor arrests and seizing the ransomware group’s equipment.
The next day, the SBU’s website became inaccessible due to a denial of services attack.
Multiple security researchers later told BleepingComputer that it was believed threat actors associated with the Egregor ransomware were performing the attacks in retaliation for the arrests.
BleepingComputer has not been able to confirm the validity of these claims.
