
A new phishing campaign that targets German e-banking users has been underway in the last couple of weeks, involving QR codes in the credential-snatching process.
The actors are using a range of tricks to bypass security solutions and convince their targets to open the messages and follow the instructions.
The relevant report comes from researchers at Cofense, who sampled several of these messages and mapped the actors’ tactics in detail.
A clean delivery
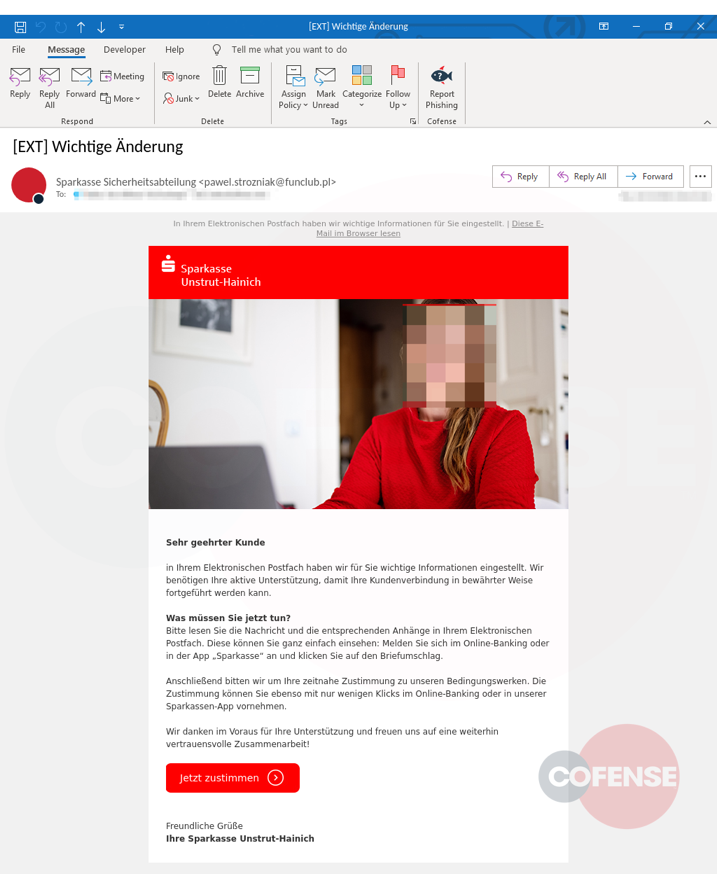
The phishing emails are carefully crafted, featuring bank logos, well-structured content, and a generally coherent style.
Their topics vary, from asking the user to consent to data policy changes implemented by the bank or requesting them to review new security procedures.
Source: Cofense
This approach is a sign of careful planning, where the actors aren’t making the typical overblown claims of account compromise and don’t present the user with an urgent situation.
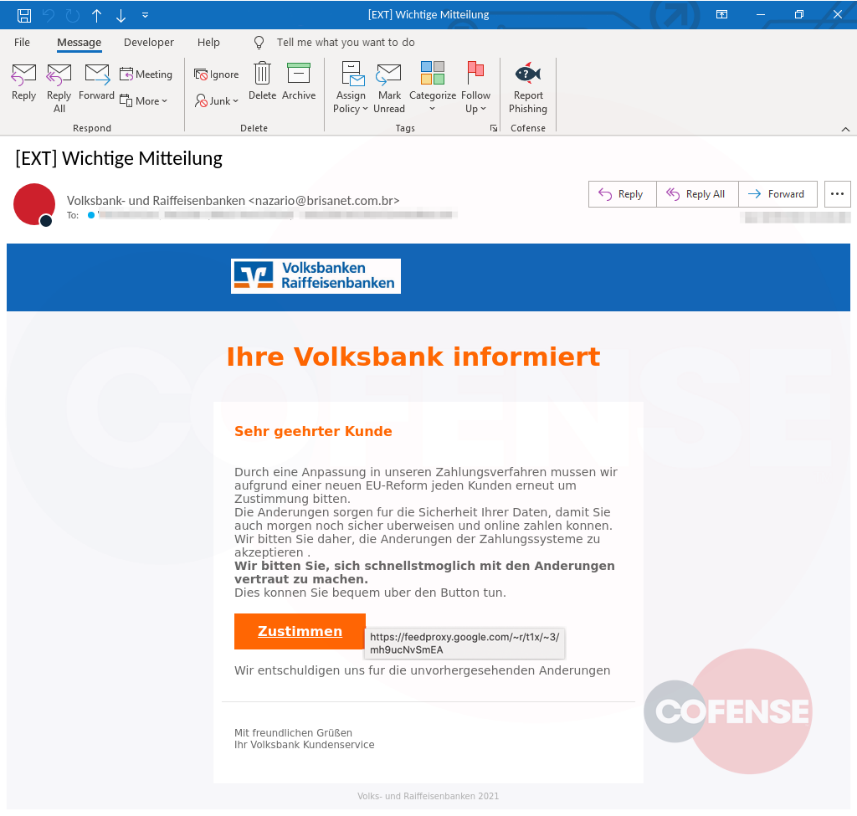
If the embedded button is clicked, the victim arrives at the phishing site after passing through Google’s feed proxy service ‘FeedBurner.’
Source: Cofense
Additionally, the actors register their own custom domains that are used for these re-directions as well as for the phishing sites themselves.
This extra step aims to trick email and internet security solutions into not raising any flags during the phishing process.
The domains are newly registered sites on the REG.RU Russian registrar and follow a standard URL structure depending on the targeted bank.
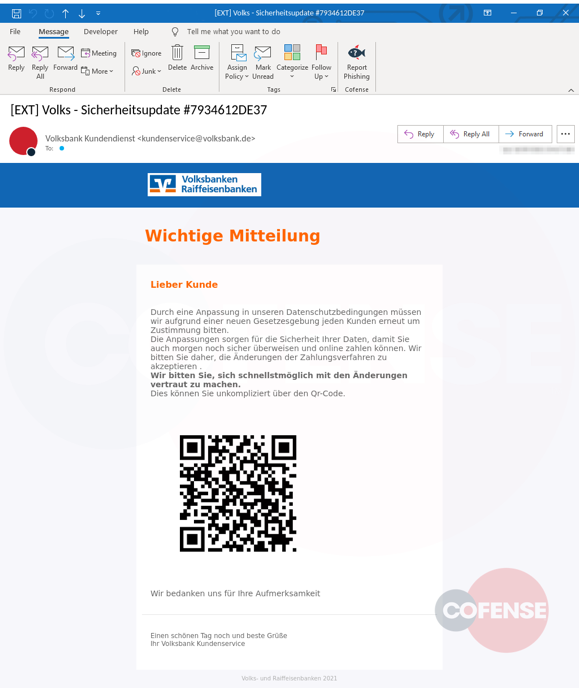
Scan this QR code to give us your credentials
In the most recent phishing campaigns, the threat actors use QR codes instead of buttons to take victims to phishing sites.
These emails do not contain clear-text URLs and are instead obfuscated through the QR codes, making it hard for security software to detect them.
Source: Cofense
QR codes have increased effectiveness as they are targeting mobile users, who are less likely to be protected by internet security tools.
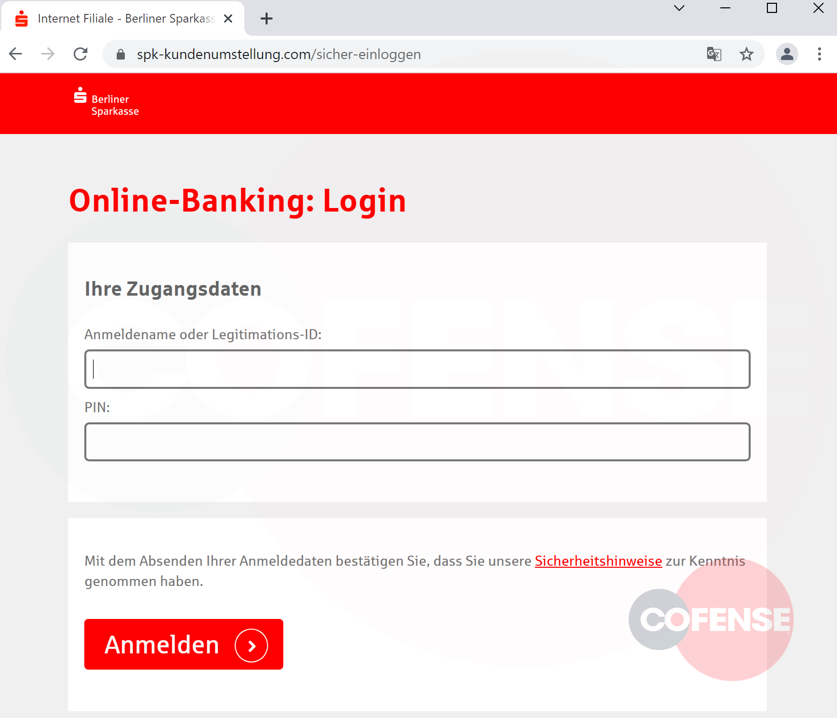
Once the victim arrives on the phishing site, they are requested to enter their bank location, code, user name, and PIN.
Source: Cofense
If these details are entered on the phishing page, the user waits for validation and then is prompted to enter their credentials again due to them being incorrect.
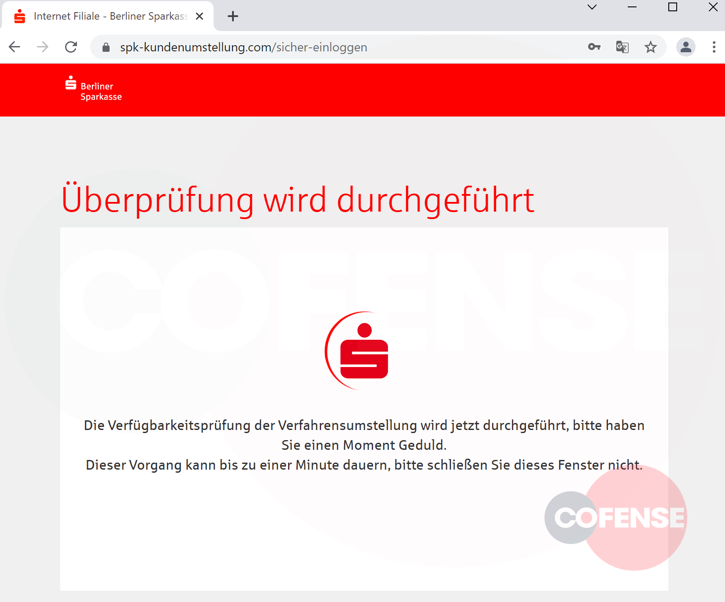
Source: Cofense
This repetition is a common quality tactic in phishing campaigns to eliminate typos when the user enters their credentials the first time.
No matter how legitimate an email may look, you should avoid clicking on buttons, URLs, or even QR codes that will take you to an external site.
Whenever you are requested to enter your account credentials, always remember to first validate the domain you are on before you start typing.
