
Critical and high severity vulnerabilities in the Responsive Menu WordPress plugin exposed over 100,000 sites to takeover attacks as discovered by Wordfence.
Responsive Menu is a WordPress plugin designed to help admins create W3C compliant and mobile-ready responsible site menus.
Flaws patched last month
In all, the Wordfence Threat Intelligence team found three vulnerabilities that can be exploited by attackers with basic user permissions to upload arbitrary files and remotely execute arbitrary code.
The first flaw enables authenticated attackers to upload arbitrary files which eventually allows them to achieve remote code execution.
The other two vulnerabilities allow a potential threat actor to forge requests to modify plugin settings of the plugin which, in turn, allows them to upload arbitrary files allowing for remote code execution.
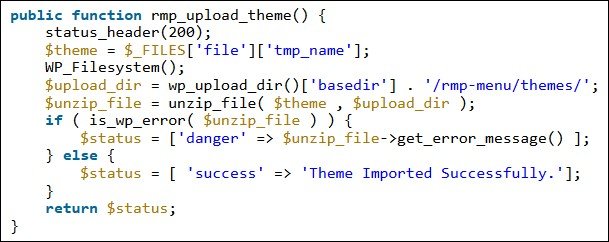
To abuse the critical vulnerability, attackers logged in as subscribers or another low-level user have to upload menu themes archived as ZIP files and containing malicious PHP files.
After the archive is extracted for installation, the attacker can access the files via the site frontend to remotely execute the malicious code which ultimately can lead to a full site takeover.
ExpressTech, the company behind Responsive Menu, patched the security issues on January 19, 2021, following multiple contact attempts between December 17 and January 4.
The report inquiries were eventually answered on January 10, after Wordfence escalated to the WordPress Plugins team.
Since the security issues impact Responsive Menu versions 4.0.0 up to 4.0.3 (or running in legacy mode), users are advised to immediately update to version 4.0.4 that addresses the bugs to prevent exploitation attempts.
“All three vulnerabilities could lead to a site takeover, which could have consequences including backdoors, spam injections, malicious redirects, and other malicious activities,” Wordfence added.
Roughly 50,000 sites still exposed to attacks
Even though Responsive Menu 4.0.4, the patched version, was released on January 19, just over 50,000 new downloads have been recorded until yesterday based on stats available on the WordPress plugin’s repository.
Since these numbers include both updates and new installs, almost 50,000 WordPress sites using Responsive Menu can still be hijacked by attackers.
Earlier this week, Wordfence also reported two critical and high severity CSRF vulnerabilities in the NextGen Gallery plugin that let hackers inject backdoors, create rogue admins, and potentially take over 530,000 WordPress sites still running unpatched plugin versions.
WordPress should install plugin security updates as soon as possible after they’re released by developers seeing that threat actors frequently exploit already fixed vulnerabilities in outdated WordPress plugins in their attacks.
